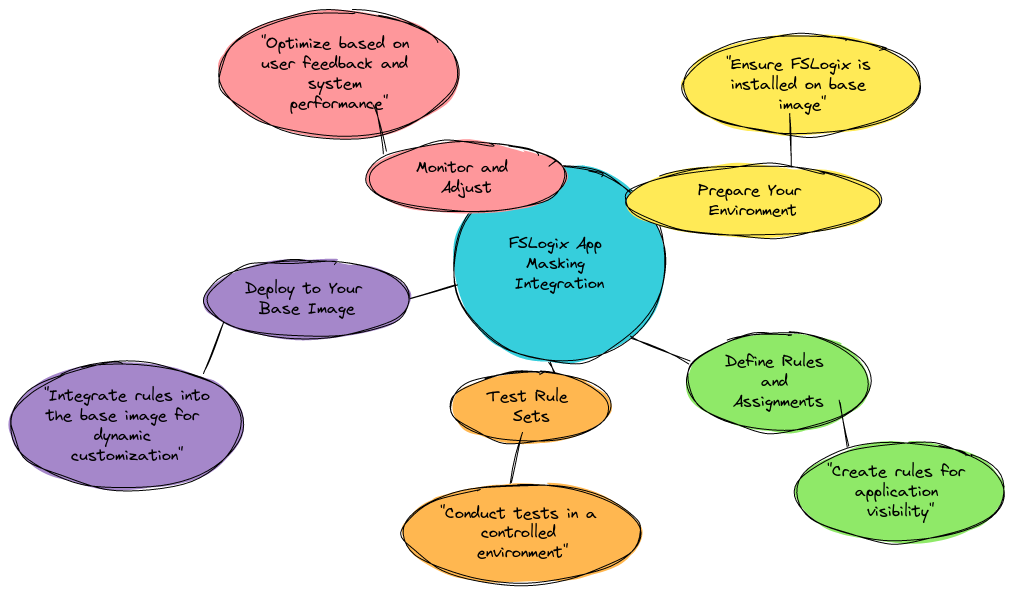
Smishing: How Scammers Use Text Messages to Trick You
In today's digital age, our smartphones have become an integral part of our daily lives. We use them for everything from communication and entertainment to banking and shopping. Unfortunately, this reliance on mobile technology has also made us vulnerable to a growing threat known as "smishing" - a type of phishing attack that uses text messages (SMS) to lure victims into revealing sensitive information or downloading malware.
Smishing attacks are becoming increasingly common as cybercriminals recognize the potential of exploiting the trust and convenience associated with text messaging. These scams often appear to come from legitimate businesses or organizations, making it challenging for unsuspecting victims to detect the deception. In this comprehensive guide, we'll explore what smishing is, how it works, and most importantly, provide you with practical strategies to protect yourself from falling victim to these insidious attacks.
What is Smishing?
Smishing is a portmanteau of "SMS phishing," where attackers use text messages to trick their targets into performing a desired action, such as clicking on a malicious link or downloading a harmful attachment. These messages are designed to appear as though they're coming from a trusted source, like a bank, a government agency, or a well-known company.
The main goal of a smishing attack is to steal sensitive information, such as login credentials, financial details, or personal identification numbers (PINs), which can then be used for fraudulent activities or to spread malware on the victim's device. Smishing attacks can also be used to direct victims to fake websites that mimic legitimate ones, where they're prompted to enter their login credentials or other sensitive data.
How Smishing Works
Smishing attacks typically follow a similar pattern:
Luring the Victim: The attacker sends a text message that appears to be from a legitimate organization, such as a bank, a delivery service, or a government agency. The message may claim that there's a problem with the victim's account, a package delivery issue, or a tax refund waiting to be claimed.
Creating a Sense of Urgency: The message often creates a sense of urgency, prompting the victim to act quickly to resolve the issue. This tactic is designed to bypass the victim's critical thinking and encourage them to respond without thoroughly evaluating the message.
Directing the Victim to a Malicious Link or Attachment: The text message will typically include a link or an attachment that the victim is instructed to click or download. These can be used to install malware on the victim's device, redirect them to a fake website, or collect sensitive information.
Exploiting the Victim: Once the victim has clicked on the link or downloaded the attachment, the attacker can gain access to the victim's device, steal their personal information, or use their device to launch further attacks.
Smishing attacks can be highly sophisticated, with cybercriminals using techniques like spoofing (making the message appear to come from a legitimate source) and social engineering (exploiting human psychology to manipulate the victim) to increase the chances of success.
Protecting Yourself from Smishing Attacks
Recognizing and avoiding smishing attacks is crucial in today's digital landscape. Here are some effective strategies to help you stay safe:
Be Wary of Unsolicited Messages Legitimate organizations will rarely initiate contact with you via text message, especially if the message is requesting sensitive information or immediate action. If you receive an unexpected message that seems to be from a company or government agency, take a moment to verify its authenticity before responding.
Inspect the Message for Red Flags
- Poor spelling, grammar, or formatting: Legitimate messages from organizations are typically well-written and professionally presented.
- Urgent or threatening language: Scammers often try to create a sense of panic or urgency to pressure victims into taking action.
- Requests for personal information: Legitimate companies will not ask for sensitive details like account numbers, Social Security numbers, or login credentials via text message.
- Unfamiliar or suspicious-looking links or attachments: Avoid clicking on any links or downloading attachments unless you're absolutely certain they're safe.
Verify the Source
If the message appears to be from a specific company or organization, take the time to contact that entity directly using a known, trusted phone number or website. Do not use the contact information provided in the suspicious text message, as it may be part of the scam.
Don't Click on Links or Download Attachments
One of the most common tactics used in smishing attacks is to include a malicious link or attachment that, when clicked or downloaded, can infect your device with malware or direct you to a fake website. Resist the temptation to interact with these elements, even if the message seems urgent or convincing.
Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your online accounts by requiring a second form of verification, such as a code sent to your phone or a biometric scan. This makes it much more difficult for attackers to gain unauthorized access to your accounts, even if they manage to obtain your login credentials.
Keep Your Devices and Software Up-to-Date
Regularly updating your smartphone's operating system, as well as any apps and security software, can help protect you from known vulnerabilities that cybercriminals may try to exploit.
Enable automatic updates
Whenever possible, ensure your devices are always running the latest, most secure versions of your software.
Use a Reputable Antivirus/Anti-Malware Solution
Install a trusted antivirus or anti-malware program on your smartphone and keep it up-to-date. These tools can help detect and block malicious files or websites, providing an additional layer of protection against smishing attacks.
Consider Using a VPN
A Virtual Private Network (VPN) can help protect your online activities, including any links or downloads you may encounter from suspicious text messages. By encrypting your internet traffic, a VPN can prevent attackers from intercepting your data or redirecting you to malicious websites.
Be Cautious with Public Wi-Fi
Public Wi-Fi networks can be vulnerable to snooping and attacks, making them a potential target for cybercriminals. Avoid clicking on any links or downloading attachments while connected to public Wi-Fi, as this can increase the risk of falling victim to a smishing scam.
Trust Your Instincts
If a text message seems too good to be true, or if something just doesn't feel right about it, trust your gut and err on the side of caution. It's better to miss out on a legitimate opportunity than to fall victim to a smishing attack.
Educating Yourself and Your Loved Ones
Protecting yourself from smishing attacks is not just about individual vigilance; it's also about educating your family, friends, and colleagues. Share this information with the people you care about, and encourage them to be equally cautious when it comes to suspicious text messages.
Consider the following strategies to help spread awareness and promote smishing prevention:
Discuss Smishing Risks
Have open conversations about the risks of smishing attacks and the tactics cybercriminals use to trick victims. Encourage your loved ones to be skeptical of unsolicited messages and to always verify the source before taking any action.
Provide Real-World Examples
Sharing specific examples of smishing scams can help illustrate the problem and make it more tangible for your audience. This can help them better recognize the warning signs in the future.
Emphasize the Importance of Verification
Stress the importance of verifying the source of any message that requests sensitive information or immediate action. Encourage your loved ones to take the time to contact the organization directly using a known, trusted method, rather than relying solely on the information provided in the text message.
Recommend Protective Measures
Provide your family and friends with the tips and strategies outlined in this guide, such as enabling two-factor authentication, keeping devices and software up-to-date, and using a reputable antivirus solution. Encourage them to implement these protective measures on their own devices and to share the information with others.
Foster a Culture of Awareness
By consistently discussing the threat of smishing and promoting best practices, you can help create a culture of awareness and vigilance within your social and professional circles. This can go a long way in reducing the success of these scams and protecting the people you care about.
Reporting and Responding to Smishing Attacks
Despite your best efforts to avoid smishing attacks, it's possible that you or someone you know may still fall victim to one. In such cases, it's important to take immediate action to mitigate the potential damage and report the incident to the appropriate authorities.
Here's what you should do if you suspect you've been the target of a smishing attack:
- Do Not Respond to the Message - Refrain from replying to the suspicious text message or engaging with the attacker in any way. Responding could potentially escalate the situation or provide the attacker with additional information to exploit.
- Do Not Click on Links or Download Attachments -If you haven't already, avoid clicking on any links or downloading any attachments from the suspicious message. This can help prevent the attacker from gaining access to your device or personal information.
- Change Passwords and Sensitive Information - If you've already provided any sensitive information, such as login credentials or financial details, change those passwords and account details immediately. This can help limit the attacker's ability to misuse the compromised information.
- Report the Incident - Contact the organization or company that the message claimed to be from, and report the incident. Many reputable companies have dedicated teams or procedures for handling and investigating such cases.
- File a Report with the Appropriate Authorities - Depending on the nature and scope of the smishing attack, you may also want to file a report with the relevant authorities, such as the Federal Trade Commission (FTC) or the Federal Communications Commission (FCC) in the United States, or your local law enforcement agency.
Monitor Your Accounts and Credit Reports
Keep a close eye on your financial accounts, credit reports, and any other sensitive information for any signs of unauthorized activity. This can help you quickly detect and respond to any potential consequences of the smishing attack.
Consider Contacting Your Mobile Carrier
If the smishing attack involved the use of a specific phone number, you may want to contact your mobile service provider to report the issue. They may be able to take steps to block or investigate the number, potentially preventing further abuse.
Educate Others
Share your experience and the lessons you've learned about smishing with your friends, family, and colleagues. This can help raise awareness and prevent others from falling victim to similar attacks in the future.
Staying Vigilant in the Face of Evolving Threats
As technology continues to advance, so too do the tactics and techniques used by cybercriminals. Smishing attacks are just one example of the constantly evolving threat landscape, and it's essential that we remain vigilant and adaptable in our approach to online security.
By staying informed, implementing best practices, and fostering a culture of awareness, we can all play a vital role in protecting ourselves, our loved ones, and our communities from the dangers of smishing and other emerging cyber threats. Remember, the key to staying safe is to approach any unsolicited text message with a healthy dose of skepticism and to always verify the source before taking any action.
"Stay vigilant, stay informed, and stay safe. Together, we can make the digital world a more secure place for everyone."
Deschaine IT











.png)