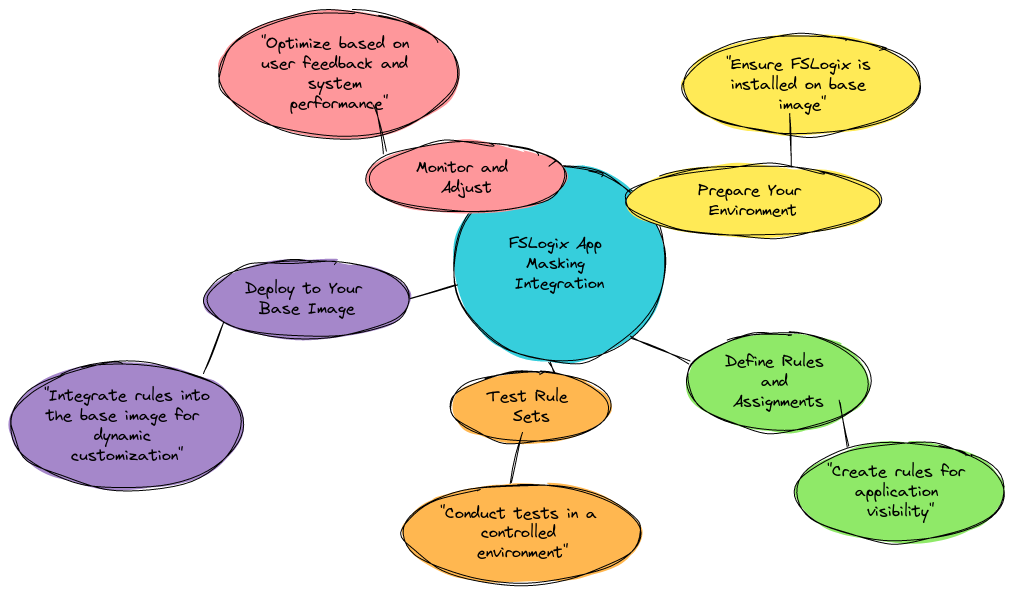
The Future of Endpoint Management: Why Zero-Trust is Critical
As organizations continue to face increasingly complex security threats, endpoint management has become an essential component of any effective cybersecurity strategy. However, as traditional endpoint management solutions struggle to keep up with the rapidly evolving threat landscape, a new approach has emerged - zero-trust.
What is Zero-Trust?
Zero-trust is a security model that assumes that all users, devices, and applications are inherently untrustworthy, and therefore should not be granted automatic access to sensitive resources. Instead, zero-trust requires continuous verification of user identity and device security before access is granted, regardless of whether the user is inside or outside the corporate network.
The Benefits of Zero-Trust
The benefits of zero-trust are clear. By implementing a zero-trust model, organizations can significantly reduce the risk of unauthorized access, data breaches, and other security incidents. But how does zero-trust relate to endpoint management, and why is it so critical?
Endpoint Management and Zero-Trust
First and foremost, endpoint management plays a crucial role in implementing a zero-trust model. By properly managing and securing endpoints, organizations can establish a secure foundation for implementing zero-trust policies. This includes:
- Ensuring that devices are up-to-date with the latest security patches
- Enforcing strong password policies
- Monitoring device health for signs of compromise.
Additionally, endpoint management can help organizations enforce zero-trust policies across all endpoints, regardless of whether they are company-owned or personal devices. This is especially critical in today's remote work environment, where employees are using a variety of devices and networks to access corporate resources.
But perhaps the most significant benefit of zero-trust endpoint management is its ability to provide continuous visibility and control over all endpoints. By constantly monitoring endpoints for signs of suspicious activity, organizations can quickly detect and respond to potential security incidents before they become major breaches.
The Bottom Line
In summary, endpoint management and zero-trust are two critical components of any modern cybersecurity strategy. By combining these two approaches, organizations can establish a strong foundation for securing their endpoints and protecting against the latest security threats.
If you're interested in learning more about endpoint management and zero-trust, please don't hesitate to reach out. I'm always happy to share my expertise and help organizations implement effective security solutions.
In Summary
Endpoint security is a complex and ever-evolving field, with a wide range of factors to consider. Some of the key areas to focus on when it comes to endpoint security include:
Vulnerability Management: Regularly scanning and patching endpoints for known vulnerabilities is critical to preventing security incidents.
Data Encryption: Encryption of sensitive data is important to ensure that even if endpoints are compromised, the data remains secure.
Identity Management: Ensuring that users are properly authenticated and authorized to access resources is critical to preventing unauthorized access.
Device Management: Properly managing and securing devices, both company-owned and personal, is critical to maintaining a secure endpoint environment.
Endpoint Detection and Response (EDR): Using advanced threat detection technologies can help organizations quickly detect and respond to potential security incidents.
Network Access Control (NAC): Implementing NAC solutions can help organizations enforce security policies and prevent unauthorized access to the network.
Mobile Device Management (MDM): As more employees use mobile devices to access corporate resources, properly managing and securing those devices has become increasingly important.
User Education: Ensuring that users are trained on best security practices and aware of potential security threats is critical to maintaining a secure endpoint environment.
These are just a few of the many areas to consider when it comes to endpoint security. It's important to work with experienced IT professionals who can help assess your organization's unique security needs and implement the right combination of technologies and policies to keep your endpoints secure.
To learn more about how you can secure your business with zero-trust and endpoint management, contact one of our trained IT professionals at Deschaine IT today. Our team of experts can help you assess your current security posture, identify areas for improvement, and develop a customized security strategy that meets your specific needs.
Don't wait until it's too late - take action today to protect your business from the latest security threats. Contact us now to schedule a consultation and get started.
In Summary
Endpoint security is a complex and ever-evolving field, with a wide range of factors to consider. Some of the key areas to focus on when it comes to endpoint security include:
-
Vulnerability Management: Regularly scanning and patching endpoints for known vulnerabilities is critical to preventing security incidents.
-
Data Encryption: Encryption of sensitive data is important to ensure that even if endpoints are compromised, the data remains secure.
-
Identity Management: Ensuring that users are properly authenticated and authorized to access resources is critical to preventing unauthorized access.
-
Device Management: Properly managing and securing devices, both company-owned and personal, is critical to maintaining a secure endpoint environment.
-
Endpoint Detection and Response (EDR): Using advanced threat detection technologies can help organizations quickly detect and respond to potential security incidents.
-
Network Access Control (NAC): Implementing NAC solutions can help organizations enforce security policies and prevent unauthorized access to the network.
-
Mobile Device Management (MDM): As more employees use mobile devices to access corporate resources, properly managing and securing those devices has become increasingly important.
-
User Education: Ensuring that users are trained on best security practices and aware of potential security threats is critical to maintaining a secure endpoint environment.
These are just a few of the many areas to consider when it comes to endpoint security. It's important to work with experienced IT professionals who can help assess your organization's unique security needs and implement the right combination of technologies and policies to keep your endpoints secure.
To learn more about how you can secure your business with zero-trust and endpoint management, contact one of our trained IT professionals at Deschaine IT today. Our team of experts can help you assess your current security posture, identify areas for improvement, and develop a customized security strategy that meets your specific needs.
Don't wait until it's too late - take action today to protect your business from the latest security threats. Contact us now to schedule a consultation and get started.












.png)